What is the NIST Cybersecurity Framework?
As detailed in my previous blog, the framework integrates industry standards and best practices to help organizations manage their cybersecurity risks. It provides a common language that allows staff at all levels within an organization—including customers and partners—to develop a shared understanding of their cybersecurity risks.
The framework consists of five functions that contain 23 categories and 108 subcategories:
- Identify
- Protect
- Detect
- Respond
- Recover
This article will focus on one category and subcategory in the Identify function and how Tachyon can address these items.
A day in the life of a Tachyon Admin
Today, like every other day, I wake up and drink coffee everyday while I scan my inbox. With my inbox finally manageable, I surf my regular cybersecurity websites to find out about current events and get an alert that Adobe has just released a critical security update to Flash Player. In my environment, we have many devices with Flash Player installed and I see that version 32.0.0.433 and earlier need this update.
At this point, I don’t know if I need to be concerned about my environment or if I need prioritize this update. I need some additional information so that I can formulate my actions. Without Tachyon, I would react in one of two ways:
- Leave my environment vulnerable, thinking, "I know we told everyone to update their Flash Player."
- Create a panic and rush this update to deployment.
With Tachyon, the choice is: remain calm. I open Explorer and ask the question, "Which versions of Flash Player are installed?"
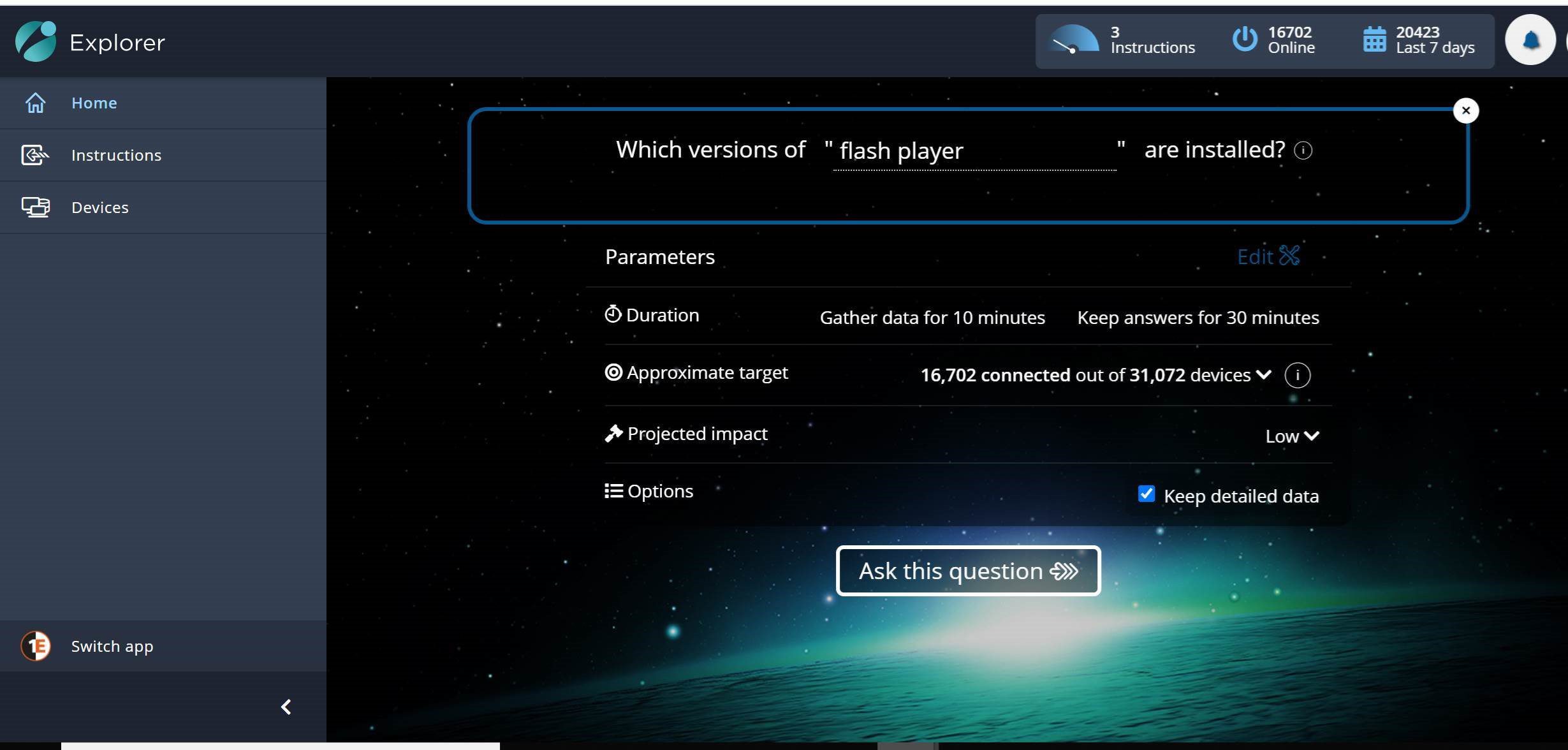
I click "Ask this question," and Tachyon returns my counts of versions in seconds.
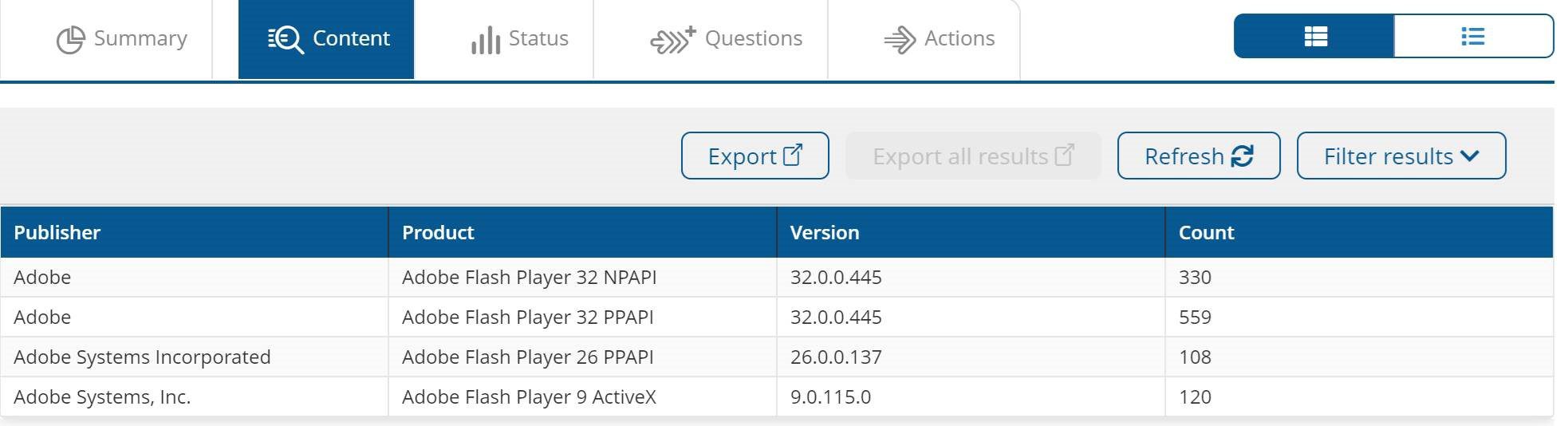
This identification of the software installed on the devices in your environment is another critical foundation of any cybersecurity program. Tachyon's ability to provide this data in real-time is key to allowing you to keep your environment secure.
- As you can see, I have 228 devices in my environment that don’t have the update (they have a vulnerable version of Flash Player). Here are the next steps I take:
- Ask another question and get the list of the device names, just as fast.
- Perform a follow-up action to target those systems with a Tachyon instruction to deploy the update. Since I have System Center Configuration Manager (SCCM) integrated with Tachyon in my environment, I deploy the update in SCCM.
- Ask the question, "Which devices have the prior versions of Flash Player installed?" from directly within my SCCM console. I can then create a collection based on the responses and deploy my package to that collection.
Yes, it’s that simple—and fast.
Cybersecurity is more important now in our work from anywhere world than it has ever been. 1E has helped many organizations adopt a cybersecurity framework and implement solutions to fulfill the framework's technical goals. To learn more, speak to a 1E expert.




