Welcome to the first of a three-part series on Device Guard!!
Judging by the number of tweets in the last couple of months which include the hashtag #DeviceGuard, you may conclude that this important and game-changing feature in Windows 10 security might be…well, not be that important. Don't be fooled.
In this three part series on the blog, we’ll be covering the following:
Part 1: Introducing the problem
- Why antimalware and antivirus are not enough
- What is Device Guard designed to achieve?
Part 2: The theory
- What does Device Guard do and how does it do it?
- What are the risks of not using it?
Part 3: The practice
- What are the prerequisites for Device Guard?
- How to best implement Device Guard
- What's next? Is there more to be done?
Why antimalware and antivirus are not enough
Since the early days of Windows Update and the release of Windows XP SP2 (i.e. introduction of Windows Firewall), Microsoft has improved its position on endpoint security. First, it acquired an anti-spyware product (which later became Windows Defender) when information theft and "spying" on online activities was the primary concern of the day. With the proliferation of threats such as complex viruses, Microsoft later responded by adding an anti-virus engine to Windows Defender. Progress has continued to where now, Windows Defender is automatically installed with Windows 8 and 10 installations. These advances have been "good enough" for consumer and small-business customers, but are lacking as a true enterprise solution.
The Ponemon Institute conducted a survey in January 2015 and a key finding revealed the following:
"On average, organizations receive almost 17,000 malware alerts in a typical week but only 19 percent of these alerts are deemed to be reliable. Of the 3,218 reliable alerts, only 705 are investigated. This suggests that participating organizations do not have the resources or in-house expertise to detect or block serious malware." – Ponemon Institute: The Cost of Malware Containment
The reactive nature of endpoint security is becoming increasingly ineffective for the enterprise. To be a step ahead of the bad actors, an omniscient strategy would be required. But this is clairvoyant, the holy grail of endpoint security! Is this even possible?
A well-executed implementation of Device Guard nearly makes this a reality. Let me explain…
What is Device Guard designed to achieve
Today's endpoint security products are evolving, but are still heavily dependent upon signature-based strategies in detecting "known" threats. This is a reactive approach, meaning the "signature" of the malware or virus has to be known before it can be detected and dealt with. Sixty-nine percent of respondents to the Ponemon Institute survey sayvendor supplied information is their main source of intelligence about malware threats followed by sixty-four percent who become educated through peer communications and community involvement. It is this aspect of signature-based solutions that creates the most exposure to risk for organizations: waiting on others before solving the problem.
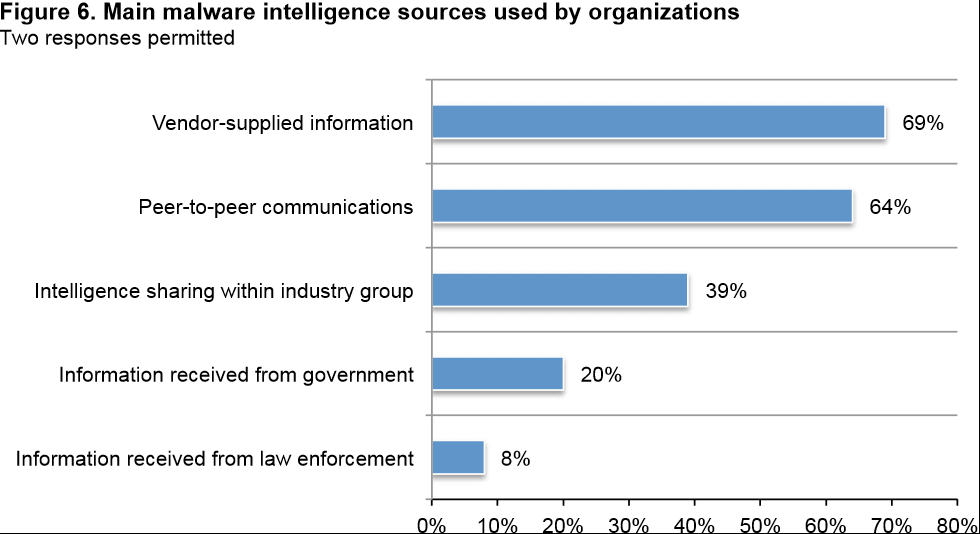
Slow response perpetuates risk
Once signature databases are updated by the endpoint security vendors, it can take some time before customers finally get the updated signature deployed in the enterprise. Sixty-three percent of the Ponemon survey respondents say they either have an unstructured or "ad hoc" approach to malware containment, or they have a structured approach but it has dependency on "manual" (reactive) activities.
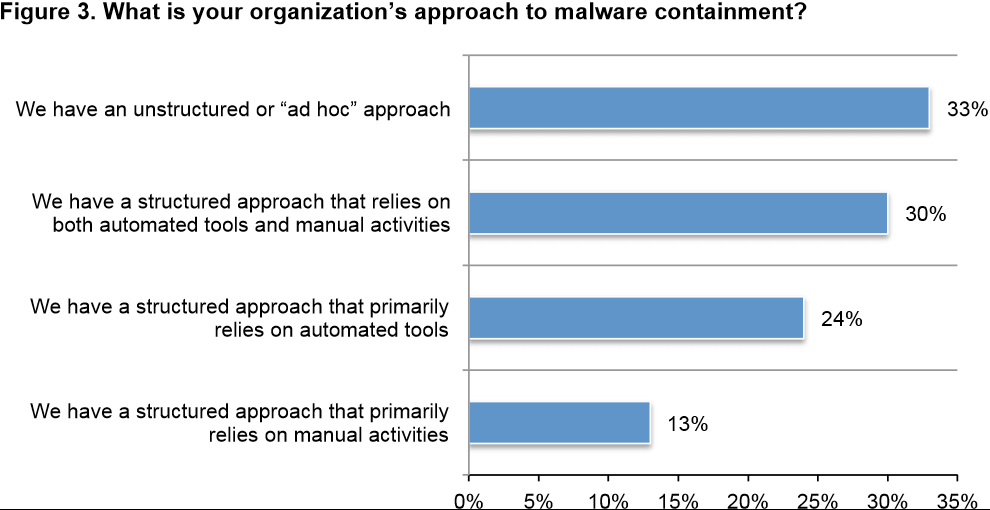
Whitelist for the Enterprise
Device Guard equips organizations with a robust, centrally-managed, proactive endpoint protection framework that only allows authorized processes and software to run, rather than blindly trusting all software and waiting for signature-based tools to detect and block the threat from further execution.
Saying it differently, signature-based products "allow everything to run and detect known-bad, preventing its execution" – reactive, while Device Guard says "nothing is allowed to run except what is known and trusted" – proactive. Device Guard's actions are governed by a rules-based system defined in policies created by the customer, rather than depending upon security vendors and the community to stay informed before taking corrective action. When Device Guard enforces a mitigation policy on an unknown/untrusted process, the threat is neutralized instantly.
Think of Device Guard as an effective "whitelist" service.
Summary
To summarize the key points of this first part of the series:
- Endpoint security in Windows has evolved, but a true enterprise solution has been lacking
- Solely relying on 3rd party vendor solutions and community-centric intelligence for endpoint security puts organizations in a reactive position
- Windows 10 Device Guard equips enterprises to be proactive, with a more modernized defense strategy for endpoint security
Want to learn more? Read, Part 2 Device Guard: The Theory, where I’ll be covering:
- What does Device Guard do and how it does it do it?
- What are the risks of not using it?
To learn more about Windows 10 and ConfigMgr migration topics from 1E, register for upcoming webinars and watch recorded webinars:
Upcoming Webinar Series:
Recorded Webinars:








